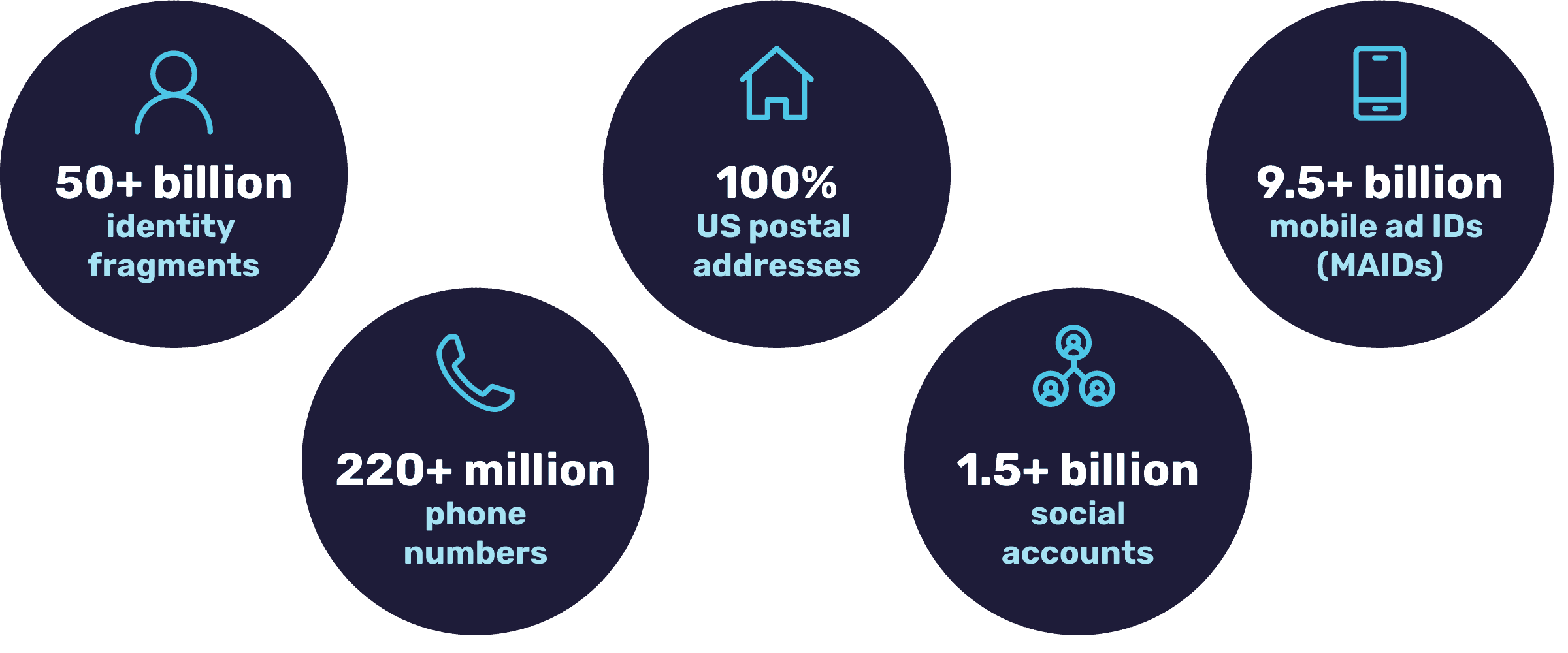
Our Graph is SECURE
Given the nature of our work, security is paramount, and protecting data is critical. It is our duty to secure personal and sensitive information. This starts from the ground up and is embedded in our culture.
We’ve implemented processes and technologies around:
- Data encryption
- Controlled access to sensitive data
- Employee training
- Rigorous background checks
FullContact invests in and maintains the highest level of data security. We’ve created numerous security measures, activated per-account encryption to keep account-specific information locked up, and added an audit trail for decryption requests.
We’re SOC2 Type II certified, which is considered the most comprehensive certification under SOC protocols. SOC 2 Type II builds on SOC 1, while additionally requiring a third- party audit, standard operating procedures for organizational oversight, vendor management, risk management, and regulatory oversight. To earn this designation, we went through a rigorous evaluation over the course of a year and are actively maintaining its certification.
We take data privacy so seriously that we were poised and ready to comply with CCPA and GDPR requirements. We have chosen to take the stance that these guidelines apply to everyone—not just those individuals who fall under the CCPA and GDPR protections.
Why? Because it’s the right thing to do.
We had the pleasure of winning the Advisory Board of Privacy Council Award in 2018.